Evil bit (nonfiction): Difference between revisions
Jump to navigation
Jump to search
No edit summary |
|||
| (8 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
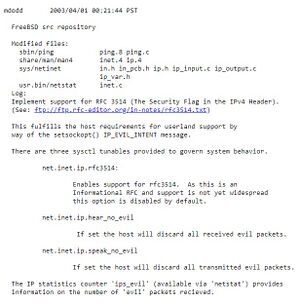
The '''evil bit''' is a [[Fiction (nonfiction)|fictional]] IPv4 packet header field proposed in RFC 3514, a humorous April Fools' Day RFC from 2003 authored by Steve Bellovin. | [[File:RFC 3514 IP EVIL INTENT.jpg|thumb|Screenshot of the April Fool's Day implementation of the RFC 5314 'Evil Bit' protocol.]]The '''evil bit''' is a [[Fiction (nonfiction)|fictional]] IPv4 packet header field proposed in RFC 3514, a humorous April Fools' Day RFC from 2003 authored by Steve Bellovin. | ||
The RFC recommended that the last remaining unused bit in the IPv4 packet header be used to indicate whether a packet had been sent with | The RFC recommended that the last remaining unused bit in the IPv4 packet header be used to indicate whether a packet had been sent with malicious intent, thus making computer security engineering an easy problem -- simply ignore any messages with the evil bit set. | ||
== In the News == | == In the News == | ||
<gallery | <gallery> | ||
File:Sweet, sweet crude oil.jpg|link=Sweet, sweet crude oil|August 20, 2018: Rogue military chemist tell reporters that [[Sweet, sweet crude oil]] is "mostly ordinary crude oil and [[Extract of Radium]], with traces of [[Evil bit (nonfiction)|evil bits]] and God knows what else." | |||
File:Fugitive Rubies and hand x-ray.jpg|link=Evil bit release|This photograph, if genuine, may show the moment following the [[Evil bit release|release of an evil bit]] by alleged supervillain [[Fugitive Rubies]]. | |||
</gallery> | </gallery> | ||
| Line 11: | Line 13: | ||
* [[Carnevale Tenebre]] | * [[Carnevale Tenebre]] | ||
* [[Evil bit release]] | |||
* [[Gnomon Algorithm]] | * [[Gnomon Algorithm]] | ||
* [[Hollerith]] | * [[Hollerith]] | ||
* [[Killer Poke]] - software defect | * [[Killer Poke]] - software defect and contract killer for hire. | ||
* [[Malvoleum]] - an evil grease derived from [[Sweet, sweet crude oil]]. | |||
* [[Murder, Incorporated 1.1]] | |||
* [[One If By Good, Zero If By Evil]] | |||
* [[Ticketology]] | * [[Ticketology]] | ||
Latest revision as of 17:00, 14 September 2018
The evil bit is a fictional IPv4 packet header field proposed in RFC 3514, a humorous April Fools' Day RFC from 2003 authored by Steve Bellovin.
The RFC recommended that the last remaining unused bit in the IPv4 packet header be used to indicate whether a packet had been sent with malicious intent, thus making computer security engineering an easy problem -- simply ignore any messages with the evil bit set.
In the News
August 20, 2018: Rogue military chemist tell reporters that Sweet, sweet crude oil is "mostly ordinary crude oil and Extract of Radium, with traces of evil bits and God knows what else."
This photograph, if genuine, may show the moment following the release of an evil bit by alleged supervillain Fugitive Rubies.
Fiction cross-reference
- Carnevale Tenebre
- Evil bit release
- Gnomon Algorithm
- Hollerith
- Killer Poke - software defect and contract killer for hire.
- Malvoleum - an evil grease derived from Sweet, sweet crude oil.
- Murder, Incorporated 1.1
- One If By Good, Zero If By Evil
- Ticketology
Nonfiction cross-reference
External links:
- Evil bit @ Wikipedia