Cryptography (nonfiction): Difference between revisions
No edit summary |
No edit summary |
||
| (One intermediate revision by the same user not shown) | |||
| Line 36: | Line 36: | ||
* [http://en.wikipedia.org/wiki/Cryptography Cryptography] @ Wikipedia | * [http://en.wikipedia.org/wiki/Cryptography Cryptography] @ Wikipedia | ||
* [https://www.coursera.org/learn/crypto Cryptography I] @ Coursera | * [https://www.coursera.org/learn/crypto Cryptography I] @ Coursera | ||
* [https://boingboing.net/2019/09/10/rule-of-law-security.html Creating a "coercion resistant" communications system] @ Boing Boing - "... systems designers [should] contemplate ways to arbitrage both the rule of law and technical pre-commitments to make it harder for governments to force you to weaken the security of your product or compromise your users." | |||
[[Category:Nonfiction (nonfiction)]] | [[Category:Nonfiction (nonfiction)]] | ||
[[Category:Cryptography (nonfiction)]] | [[Category:Cryptography (nonfiction)]] | ||
Latest revision as of 05:29, 13 September 2019
Cryptography (or cryptology; from Greek κρυπτός kryptós, "hidden, secret"; and γράφειν graphein, "writing", or -λογία -logia, "study", respectively) is the practice and study of techniques for secure communication in the presence of third parties (called adversaries).
More generally, it is about constructing and analyzing protocols that block adversaries.
Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, and electrical engineering.
Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense.
The originator of an encrypted message shared the decoding technique needed to recover the original information only with intended recipients, thereby precluding unwanted persons from doing the same.
Since World War I and the advent of the computer, the methods used to carry out cryptology have become increasingly complex and its application more widespread.
In the News
Cryptographic numen modelled in nanowire.
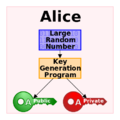
Diagram of public-key cryptography generation refuses to disclose private key.
Fiction cross-reference
- Cryptographic numen - a numen (nonfiction) arising from cryptography.
- Casio + N = CasiNo
- Gnomon algorithm
- Gnomon Chronicles
Nonfiction cross-reference
- Alberti cipher (nonfiction)
- Mathematics (nonfiction)
- Oblivious transfer (nonfiction) - an oblivious transfer (OT) protocol is a protocol in which a sender transfers one of potentially many pieces of information to a receiver, but remains oblivious as to what piece (if any) has been transferred.
- Steganography (nonfiction)
External links:
- Cryptography @ Wikipedia
- Cryptography I @ Coursera
- Creating a "coercion resistant" communications system @ Boing Boing - "... systems designers [should] contemplate ways to arbitrage both the rule of law and technical pre-commitments to make it harder for governments to force you to weaken the security of your product or compromise your users."