Gnomon algorithm: Difference between revisions
No edit summary |
No edit summary |
||
| (24 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
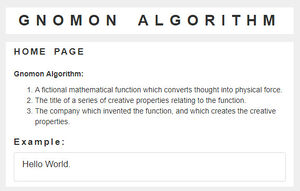
The '''Gnomon algorithm''' is a family of [[Mathematical function (nonfiction)|mathematical functions (nonfiction)]] which convert [[computation (nonfiction) | [[File:Gnomon algorithm home page screenshot.jpg|thumb|Screenshot from the gnomonalgorithn.com home page, stating the basics principles of Gnomon algorithm theory.]]The '''Gnomon algorithm''' is a family of [[Mathematical function (nonfiction)|mathematical functions (nonfiction)]] which convert [[computation (nonfiction)]] into [[force (nonfiction)]]. | ||
== Applications == | |||
[[Mathematicians]] use Gnomon algorithm functions for a variety of purposes: | |||
* Detecting and preventing [[crimes against mathematical constants]] | |||
* Creating, managing, and deleting [[trandimensional corporations]] | |||
* Participating in the [[Gnomon Chronicles]] | |||
* Computational farming with [[diagramaceous soil]] | |||
* Playing [[Fantasy Voronoi diagram]] | |||
* Activating and controlling [[scrying engines]] | |||
* Communicating with [[AESOP]] | |||
== In the News == | == In the News == | ||
<gallery | <gallery> | ||
File:Charles Sanders Peirce in 1859.jpg|link=Charles Sanders Peirce (nonfiction)|[[Charles Sanders Peirce (nonfiction)|Charles Sanders Peirce]] invents new variety of Gnomon algorithm, anticipates future work by [[Ernst Schröder (nonfiction)|Ernst Schröder]].File:Guo_Shoujing_studies_the_Pleiades.jpg|[[Guo Shoujing (nonfiction)]] studies the Pleiades, discovers new form of Gnomon algorithm. | <!-- | ||
File:Binary_counter.gif|link=Computer science (nonfiction)|2018: [[Computer science (nonfiction)|Binary counter working overtime]], looking forward to that big paycheck. | |||
File:Spinning_Thistle.jpg|link=Spinning Thistle (nonfiction)|2018: Steganographic analysis ''[[Spinning Thistle (nonfiction)|Spinning Thistle]]'' unexpectedly reveals a previously unknown Gnomon algorithm function. | |||
File:Green_Spiral_9.jpg|link=Green Spiral 9 (nonfiction)|2017: Steganographic analysis of ''[[Green Spiral 9 (nonfiction)|Green Spiral 9]]'' unexpectedly reveals two terabytes of previously unknown Gnomon algorithm functions. | |||
File:Matteo_Ricci.jpg|link=Matteo Ricci (nonfiction)|1600: Priest and mathematician [[Matteo Ricci (nonfiction)|Matteo Ricci]] publish his groundbreaking translation of ''Euclid's Elements'' into Gnomon algorithm statements. | |||
File:Galileo_E_pur_si_muove.jpg|link=Galileo Galilei|Physicist and crime-fighter [[Galileo Galilei]], imprisoned on trumped-up charges, uses nail to scratch the equation ''E pur si muove'' on dungeon wall; in the process, he discovers a deliberately concealed Gnomon algorithm function which proves his innocence. Although [[Galileo Galilei|Galileo]]'s accusation that the function was stolen and concealed by the [[Forbidden Ratio]] is widely believed to be true, no proof has emerged that the [[Forbidden Ratio|Ratio]] or its degenerate cases were involved. | |||
File:Yanghui triangle.gif|link=Rod calculus (nonfiction)|1257: First known use of [[Rod calculus (nonfiction)|Yui's triangle]] to compute [[Gnomon algorithm]] functions. | |||
File:Enrico Fermi 1943-49.jpg|link=Enrico Fermi (nonfiction)|[[Enrico Fermi (nonfiction)|Enrico Fermi]] discovers new form of Gnomon algorithm, uses it predict and prevent [[crimes against mathematical constants]]. | |||
File:Charles Sanders Peirce in 1859.jpg|link=Charles Sanders Peirce (nonfiction)|[[Charles Sanders Peirce (nonfiction)|Charles Sanders Peirce]] invents new variety of Gnomon algorithm, anticipates future work by [[Ernst Schröder (nonfiction)|Ernst Schröder]]. | |||
File:Guo_Shoujing_studies_the_Pleiades.jpg|[[Guo Shoujing (nonfiction)]] studies the Pleiades, discovers new form of Gnomon algorithm. | |||
--> | |||
</gallery> | </gallery> | ||
== Quotations == | |||
[[Alice Beta]] observes: | |||
<blockquote>If we corrupt the Gnomon algorithm configuration files, all Hell breaks loose. If we fail to prevent our enemies from corrupting the configuration files, all Hell breaks loose. | |||
The files appear to be immortal and self-correcting; but we could be wrong about this, and some of us think the files are like an ecosystem, or an artificially intelligent radioisotope network: a fluctuating feature of the universe which we should, perhaps, consider taming, much as agriculture tamed food and industry tamed machines -- which is to say, agriculture tamed famine, and industry tamed the fragility of existence."</blockquote> | |||
— Source: Alice Beta lecture series. | |||
== Fiction cross-reference == | == Fiction cross-reference == | ||
* [[Crimes against mathematical constants]] | |||
* [[Havelock]] | * [[Havelock]] | ||
* [[Hollerith]] | * [[Hollerith]] | ||
* [[Mathematician]] | |||
* [[Mathematics]] | * [[Mathematics]] | ||
* [[Scrying engine]] | |||
* [[The Custodian]] | |||
* [[Transdimensional corporation]] | |||
* [[Watergate Scandal (virus)]] - a [[math virus]] which infiltrates and corrupts Gnomon algorithm functions in order to commit [[crimes against mathematical constants]] for political purposes. | |||
== Nonfiction cross-reference == | == Nonfiction cross-reference == | ||
| Line 23: | Line 69: | ||
* [[Force (nonfiction)]] | * [[Force (nonfiction)]] | ||
* [[Gnomon (nonfiction)]] | * [[Gnomon (nonfiction)]] | ||
* [[Gnomon | * [[Gnomon algorithm (nonfiction)]] | ||
* [[Mathematical function (nonfiction)]] | * [[Mathematical function (nonfiction)]] | ||
* [[Mathematics (nonfiction)]] | * [[Mathematics (nonfiction)]] | ||
* [[Measurement (nonfiction)]] | * [[Measurement (nonfiction)]] | ||
* [[Pathological science (nonfiction)]] | |||
[[Category:Fiction (nonfiction)]] | [[Category:Fiction (nonfiction)]] | ||
[[Category:Gnomon algorithm]] | [[Category:Gnomon algorithm]] | ||
Latest revision as of 04:04, 24 August 2020
The Gnomon algorithm is a family of mathematical functions (nonfiction) which convert computation (nonfiction) into force (nonfiction).
Applications
Mathematicians use Gnomon algorithm functions for a variety of purposes:
- Detecting and preventing crimes against mathematical constants
- Creating, managing, and deleting trandimensional corporations
- Participating in the Gnomon Chronicles
- Computational farming with diagramaceous soil
- Playing Fantasy Voronoi diagram
- Activating and controlling scrying engines
- Communicating with AESOP
In the News
2018: Binary counter working overtime, looking forward to that big paycheck.
2018: Steganographic analysis Spinning Thistle unexpectedly reveals a previously unknown Gnomon algorithm function.
2017: Steganographic analysis of Green Spiral 9 unexpectedly reveals two terabytes of previously unknown Gnomon algorithm functions.
1600: Priest and mathematician Matteo Ricci publish his groundbreaking translation of Euclid's Elements into Gnomon algorithm statements.
Physicist and crime-fighter Galileo Galilei, imprisoned on trumped-up charges, uses nail to scratch the equation E pur si muove on dungeon wall; in the process, he discovers a deliberately concealed Gnomon algorithm function which proves his innocence. Although Galileo's accusation that the function was stolen and concealed by the Forbidden Ratio is widely believed to be true, no proof has emerged that the Ratio or its degenerate cases were involved.
1257: First known use of Yui's triangle to compute Gnomon algorithm functions.
Enrico Fermi discovers new form of Gnomon algorithm, uses it predict and prevent crimes against mathematical constants.
Charles Sanders Peirce invents new variety of Gnomon algorithm, anticipates future work by Ernst Schröder.
Guo Shoujing (nonfiction) studies the Pleiades, discovers new form of Gnomon algorithm.
Quotations
Alice Beta observes:
If we corrupt the Gnomon algorithm configuration files, all Hell breaks loose. If we fail to prevent our enemies from corrupting the configuration files, all Hell breaks loose. The files appear to be immortal and self-correcting; but we could be wrong about this, and some of us think the files are like an ecosystem, or an artificially intelligent radioisotope network: a fluctuating feature of the universe which we should, perhaps, consider taming, much as agriculture tamed food and industry tamed machines -- which is to say, agriculture tamed famine, and industry tamed the fragility of existence."
— Source: Alice Beta lecture series.
Fiction cross-reference
- Crimes against mathematical constants
- Havelock
- Hollerith
- Mathematician
- Mathematics
- Scrying engine
- The Custodian
- Transdimensional corporation
- Watergate Scandal (virus) - a math virus which infiltrates and corrupts Gnomon algorithm functions in order to commit crimes against mathematical constants for political purposes.
Nonfiction cross-reference
- Algorithm (nonfiction)
- Computation (nonfiction)
- Computational complexity theory (nonfiction)
- Computer science (nonfiction)
- Evil bit (nonfiction)
- Force (nonfiction)
- Gnomon (nonfiction)
- Gnomon algorithm (nonfiction)
- Mathematical function (nonfiction)
- Mathematics (nonfiction)
- Measurement (nonfiction)
- Pathological science (nonfiction)